Instagram account of a series of famous stars hacked and used as a means of fraud
The campaign to hijack celebrities' Instagram accounts after a period of cooling down has continued to heat up over the past few days, as some Instagram stars have been hacked and used as a means of fraud. islands, 'dirty' ads, or even spreading malware in the form of sitelinks.
New and most notable victims of this offensive campaign include Hollywood actor Robert Downey Jr. (43.3 million followers), singer-songwriter Nicole Scherzinger (3.9 million followers) and TV star Yanet García (11.5 million followers) - all hacked last week.
 The campaign to hijack Instagram accounts has continued to heat up recently
The campaign to hijack Instagram accounts has continued to heat up recently
- Warning: Jenkins exists a serious security hole that helps hackers gain control of computers of many Vietnamese businesses
Familiar motifs
Each of these Instagram accounts has been compromised and taken over for a short period of time, but it is enough for attackers to deploy a series of well-planned malicious activities. In particular, it is necessary to mention the act of posting fake links to spread malware or collect personal information. The collected data will then be sold for advertising purposes, usually on dark web areas.
In addition, in many cases, attackers can also earn "commissions" through generating leads for fraudulent buying or selling sites.
Most of the fraudulent activity is carried out in the following scenario: After successfully hijacking the victim's account, the attacker will immediately change the profile information, then post fraudulent content. , such as a free iPhone XS announcement or clicking on a link, declare personal information to enjoy the offer .
For example, in the case below, the space has posted a notice to donate 2,000 free Phone XS phones to the earliest subscribers, and visit the Story page to find more offers. This is the most common form of fraud.
- Stealing and selling unreleased music products, young hackers face jail time
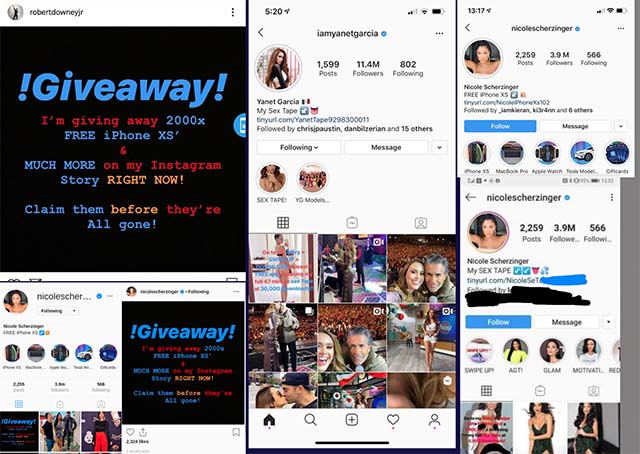 Interstitial has posted a free notice of Phone XS for those who register information at the earliest
Interstitial has posted a free notice of Phone XS for those who register information at the earliest
Hackers will use many services to shorten links with Bit.ly and TinyURL. While taking control of celebrity accounts, they will try to assign fraudulent links in the account owner's profile introduction as much as possible.
However, according to experts' verification, almost all of these links lead to several websites on the same domain, such as dudemobile.Net - showing surveys and app download requests. use. The screenshot below is the redirect links from the links posted on the hacked Instagram account of all three celebrities.
More sophisticated, when Instagram users click on the link and are redirected to the phishing site, the site will immediately be automatically translated into the language by country.
- Hackers attacked hundreds of universities to gain access to library data
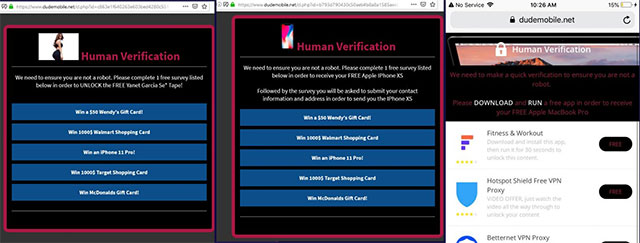 All links lead to several websites on the same domain, in this case dudemobile.Net
All links lead to several websites on the same domain, in this case dudemobile.Net
In the case of stars Nicole Scherzinger and Yanet García, hackers have created a more effective bait. They changed the content of the account's profile introduction to announce that if visitors download an app available at the provided links, they will be able to update their own 'hot' video. this language (account holder).
Or as in a fake nude photo of American singer Nicole Scherzinger, the attackers posted information that when the suite was downloaded 5,000 times, a 'hot' video would be released.
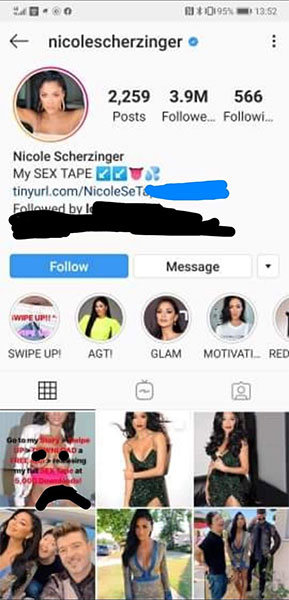 Hackers posting information will release a 'hot' video of Nicole Scherzinger
Hackers posting information will release a 'hot' video of Nicole Scherzinger
A similar scam deal was posted on the Instagram account of Mexican TV star Yanet García, but the request for the video to be released was much higher, up to 30,000 downloads.
In addition, fans accessing Yanet García's profile were also lured with a fake nude image, which was inserted with intriguing content to deceive gullible, as you can see. in the screenshot below.
- Warning: 600,000 child navigational devices may be hacked, parents should be careful
 The fake nude image of Yanet García and inserted intriguing content
The fake nude image of Yanet García and inserted intriguing content
On September 16, Yanet García posted a series of authenticated content on Twitter asking Instagram to restore control of her account from hackers.
Deepfake simulator software
It is not clear what specific software hackers have used to fake pictures of both Scherzinger and García, but experts say deepfake tools could be the answer. A basic deepfake application is usually quite cheap, only around $ 50, while still able to create very convincing images if the user is skilled.
If you do not know, deepfake is a specialized term formed by the concepts of 'deep learning' and 'fake'. This is basically a technique of synthesizing human images based on artificial intelligence (AI), which is used to combine and overlay existing images and videos onto the original images or videos by using Use a machine learning technique called the Generative Adversarial Network. Deepfake can help fake, change a person's face, thereby creating images or videos of things that this person has never done before.
This not only affects the honor and dignity of the person who has been faked image, but also made the public stir and caused controversy or possibly even worse contradictions.
- This dangerous application can penetrate women's clothing in seconds with deepfake technology
 Deepfake technology has caused a lot of controversy since the beginning
Deepfake technology has caused a lot of controversy since the beginning
In this case, the software used by hackers could easily remove clothing and create a "nude" version of the victim. It works best with high-resolution bikini images - data types that are easy to find for famous women.
It is also very difficult to penalize this deepfake software development company because it claims to release the software for "educational or demonstration purposes" and is not responsible for any damages resulting from the use of content created by application.
Since its inception, deepfake technology has caused a lot of controversy. The case of DeepNude is an example. The project made a big splash right from the start but was then forced to stop working after it started being abused for malicious purposes.
- McAfee explained how deepfake and AI are breaching cybersecurity walls
Keep your account secure
The infosec community has continuously issued countless emergency warnings for a long time about what you need to do to enhance the security of your online accounts. And before you think about using 'security support tools', know how to create a strong password and minimize the click on strange links sent to email or posted on social networking sites.
Tools like the password manager can help create strong enough strings, allowing special characters, numbers, as well as uppercase and lowercase letters to enter a single password, and allows you to use multiple complex passwords without having to remember them at the same time.
- Google currently allows G Suite administrators to disable unsafe 2FA authentication too
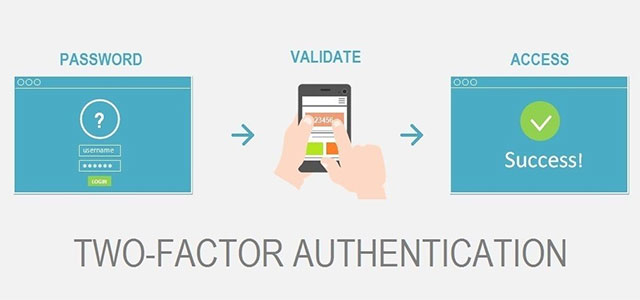 The operation of the 2-factor account authentication method
The operation of the 2-factor account authentication method
Many services now offer 2-factor authentication (2FA), a security feature that can help keep your account safe even if hackers steal part of your login information. 2FA works on the basis of requiring the account owner to authenticate by having to enter the password and providing a one-time code, usually sent to the device they own via text message or created by mobile application. In particular, the one-time code used is an additional layer of security.
This way, an attacker will not be able to log in using mere account credentials, but will have to gain additional access to your device, which makes their job much harder. much.