How to avoid DDoS attacks

There's no doubt that cyber security is a hot topicand will continue to be for the foreseeable future. This is especially true as even computer giants like Microsoft are still only just discovering gaps in their protection that have existed for two years or more.
But, over and above potential security breaches like this, it is DDoS attacks (Distributed Denial of Service) that are causing even more concern. It's been estimated that around 80% of all major companies experience an attempted attack each year. The purpose is generally to inconvenience and, in some cases destroy, the victim's business and this may or may not be for financial gain.
Who is at risk?
Image source: 888 Casino
Particularly at risk are large online organizations, news sites, universities and online services in general. Online retail giant Amazon spent two days fighting an attack in June this year which shows even the biggest of businesses can't prevent attacks from happening. Another huge sector that has become increasingly vulnerable has been the online gambling industry.
Relying, as they do, on being available for players 24/7 it means that leading operators are now taking the threat very seriously indeed and have many additional security measures in place. An example of a provider which has an array of sophisticated security measures in place to prevent DDoS attacks from happening is the excellent 888 Casino. It proves a safe and secure place to gamble, while being an engaging and well-respected online casino.
As a DDoS attack generally involves the flooding of the host website with so many requests and visits that it effectively becomes paralyzed, it can be hugely damaging for a business financially. Many users will simply go elsewhere. There are three key types of attack that businesses are most vulnerable to and these are volumetric, application layer and protocol-based.We'll explain more about each type below.
Volumetric Attacks
A volumetric attack quite simply overwhelms a site with so many queries at the same time thatall need to be resolved. But, as the site is dealing with them, more and more arrive leaving it unable to cope with any of them at all so it crashes. This is catastrophic for businesses as their customers leave the site and go to competitors.
Application layer attacks
These attack the top layer of the Open Systems Interconnection model which makes them harder to identify by the server, especially as this kind of attack can be launched by fewer machines and sometimes even a single one. The host site might just assume that it is simply experiencing a higher volume of traffic than usual when actually it is under attack.
Protocol attacks
The third example disrupts the network connections, sometimes including the 'handshake' that two computers need to complete before they can start to communicate. This leaves the connection hanging and multiple incidences of this effectively bring the system to a standstill.
As DDoS attacks become more sophisticated and larger scale, more and more measures are being devised to prevent them. Here are six typical techniques websites implement to help prevent them.
Developing a DDoS Response Plan

Being prepared in advance for a DDoS attack is one of the best things a business can do to protect themselves.
Good preparation is at the essence of this approach. For an organization, it means running through numerous scenarios and developing strategies that will best counteract any attack. At its heart is the putting together of team with clear lines of command and responsibilities. The one possible weakness in this approach is that it assumes that attacks are inevitable and will be impossible to head off by any other means.
Securing the network infrastructure
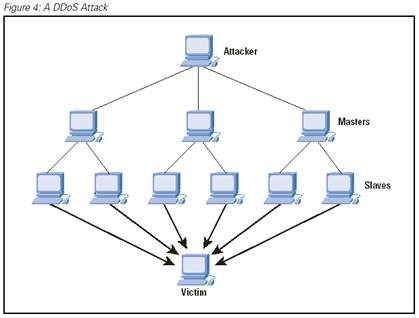
Demonstration of simultaneous attack by an army of Zombies devices on a victim target server
Hackers that plan DDoS attacks, first prepare an army of "Zombies" which are compromised devices such as internet connected cameras or other low security devices or computers. When lunching an attack, they order the slaves zombies to simultaneously send repeated requests to the target attacked server and thus causing it to collapse and deny service from its users.
This involves ensuring that there is advanced intrusion protection aligned with systems to manage threats. This can include a number of elements including VPNs, firewalls, anti-spam measures, content filters and load balancing for the system.
These can work together to both identify threats as they are developing to block the attack. It is also vital the system is kept fully updated using the very latest versions of software as out-of-date versions are a well-known area of vulnerability for network systems.
Practicing basic network security
One of the most effective ways of minimizing risk is to follow the basics. This means using strong security procedures that are commonplace in all areas of IT. These include the following:
- Setting strong passwords that are frequently changed
- Installing anti-phishing software
- Secure firewalls that limit external traffic.
While all these measureswon't prevent every DDoS attack, they are an important base level of protection to have in place.
Building strong network architecture
Building and maintaining a secure and robust network architecture is critical if security is to be achieved. This means having a network that has plenty of back-ups so that, if one server comes under attack, it can be quickly withdrawn and replaced with another.
If at all possible, servers should also be located in different places physically because the more dispersed resources are, the harder they are to attack.
Using the Cloud

Utilizing the cloud can really help businesses in the event of a DDoS attack and ensure they can counteract it quickly.
Outsourcing DDoS prevention to service providers using the cloud comes with a number of benefits. For example, the greater band width available in the cloud makes attacks harder to orchestrate. And, just like locating servers in different areas, the cloud is a diffuse resource which could be able to absorb and dissipate the malicious traffic long before it manages to do any harm.
The services are also likely to be operated by organizations who are aware of the very latest DDoS tactics and able to counteract them most effectively.
While some organizations will not want to operate in a 100% cloud-based environment, a hybrid approach is also always possible and is well worth considering.
Looking out for the warning signs
Just as an earthquake or a volcanic eruption will generate some early warning signs, there are a number of early indicators that a DDoS attack may be imminent. These may include:
- an unexpected amount of traffic on a site
- a surprising slowdown in network speed
- a weak or erratic connectivity.
These are all indicators that the actions put in place in the DDoS response plan may soon need to be deployed.
Summary
In a world in which DDoS attacks are reportedly on the rise by 180% or more, it's certainly never been more important to ensure that all the measures possible are in place to mitigate the effects that they can have. As the attacks become more and more sophisticated, not to mention widespread, this will surely become more challenging.
But,it's not a question of simply accepting that they are inevitable. With the right measures, and the growing expertise in how to nullify their effects, before long they may become less of a threat.But, until then, any business that values its security and that of its customers, will do well to be on full guard and have the correct security measures in place.