Campaign to distribute spyware aimed at macOS in Vietnam
Security experts discovered a campaign to distribute spyware with compelling content emails and attach a malicious text file to the Mac of a number of Vietnamese organizations and businesses.
Mr. Nguyen Minh Duc, Director of Information Security Company CyRadar said, when the victim opens files containing malicious code, the Macro feature of Microsoft Word will be exploited to extract a spyware that only runs on the system. macOS. The software then connects to the control server to steal information and send it to the attacker. Hackers can 'drop' other malicious code onto remote computers to control as well as a springboard to invade another computer.
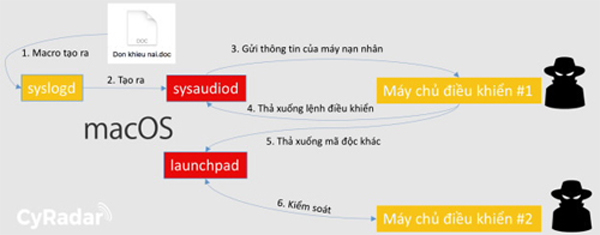
CyRadar said that the current antivirus software cannot identify malicious files in this campaign. In addition, different victims will receive different files, making detection more difficult.
Currently, the number of Mac computer users is rising, attracting the attention of hackers. Meanwhile, due to previous attacks that often target devices running Windows operating systems, many Mac users still have no habit of noticing or taking reasonable measures to lead to gaps in the system. The organization's network and can easily be exploited.
To prevent sticking malicious code on macOS computers, users need to pay attention:
- Regularly update patches for software and operating systems.
- Be careful when receiving files, strange paths via email or chat.
- Equipping prestigious security software for macOS.
- Businesses and organizations need to have network security monitoring systems to prevent, protect and promptly detect attacks on users' computers.
See more:
- 9 things to do when detecting a computer infected with malware
- Warning: a new variant of the virus that fills virtual money via Facebook Messenger will appear every 10 minutes
- The appearance of malicious code makes iMessage on iPhone be stifled and remedied
- Discover a software stealing Facebook account on the phone developed by Vietnamese hackers
- Discovered a group of hackers who use secret code to spy on 21 countries