What is COBIT? What is the role of the business?
Today's business processes are largely determined and influenced by the technologies around them. Cloud computing, big data, and social media are just a few of the technologies that play a role, while affecting an enterprise as they creating huge amounts of data. This can absolutely be used by businesses to create a competitive advantage over competitors, but also entails significant management and application challenges. This is when COBIT takes effect. So what is COBIT? What is the role and why do businesses need to understand it? We will learn together shortly.
- What is data exfiltration? How to prevent this dangerous behavior?
 COBIT has an important role in the business activities of the business
COBIT has an important role in the business activities of the business
COBIT
- COBIT definition
- The development stages of COBIT
- Core principles of COBIT 5
- The goal of COBIT
- Benefits of COBIT 5
- COBIT 5 framework
- COBIT 5 certificates
COBIT definition
COBIT is a specialized term, abbreviated for the English phrase: The Control Objectives for Information and Related Technologies (rough translation: Information management goals and related technologies), is a standard of public management. Information technology is universal, has been recognized globally, including frameworks on how to implement and practice the most appropriate information technology management (guideline).
 COBIT is a universal IT management standard
COBIT is a universal IT management standard
In simpler terms, COBIT is an IT management framework and toolkit designed to help business managers and systems narrow the gap between testing requirements. control, as well as technical challenges and business risks.
COBIT was developed and finalized by the International Association of Information Systems Auditors (ISACA) and the International Institute of Information Technology Administration (ITGI).
- What is email encryption? Why does it play an important role in email security?
The development stages of COBIT
COBIT was first introduced publicly in the mid-1990s (around 1996), with a focus on auditing practices, in particular to facilitate financial auditors in readjustment. Interact with information technology management frameworks.
Today, COBIT has developed and expanded into many other aspects, not just auditing. In particular, the third version of COBIT released by ISACA introduced more sophisticated management frameworks. The fourth edition contains the preferred standards, often used by leading IT security experts. While the latest version, COBIT 5, released in 2012, focuses more on information management, along with risk management, and is widely used in the business community.
- Overview of building an enterprise security detection and feedback system
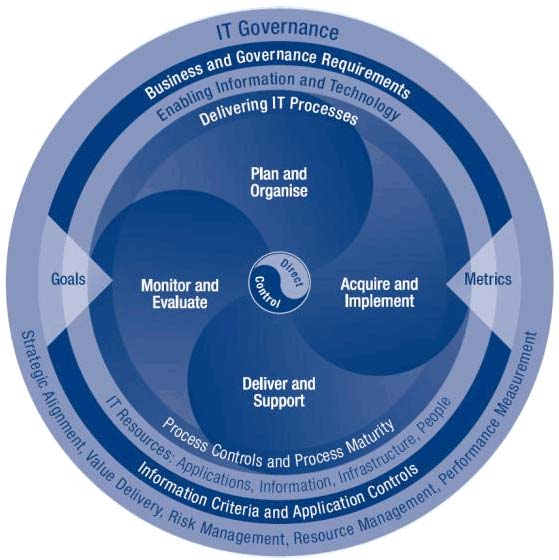
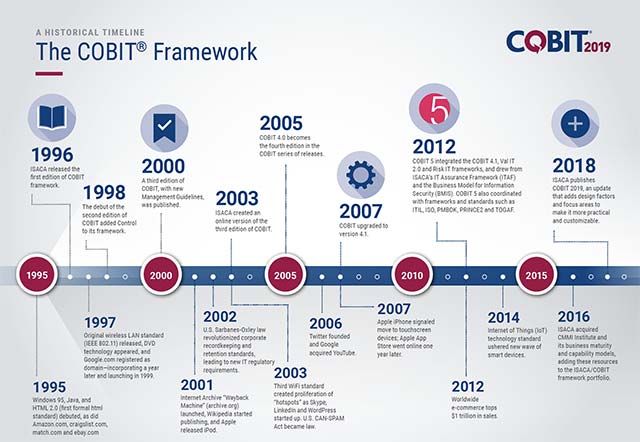 The main developmental stages of COBIT
The main developmental stages of COBIT
Core principles of COBIT 5
In this article, we will focus only on COBIT 5, the latest version and at the same time being the most concerned about this IT management standard. Basically, COBIT 5 will operate based on the following 5 core principles:
- Meeting the needs of stakeholders (shareholders, partners).
- There is a comprehensive coverage for organizations and businesses.
- Create an absolute, unified framework.
- Create a more holistic approach to the business activities of the business.
- Indicate the difference between management and governance.
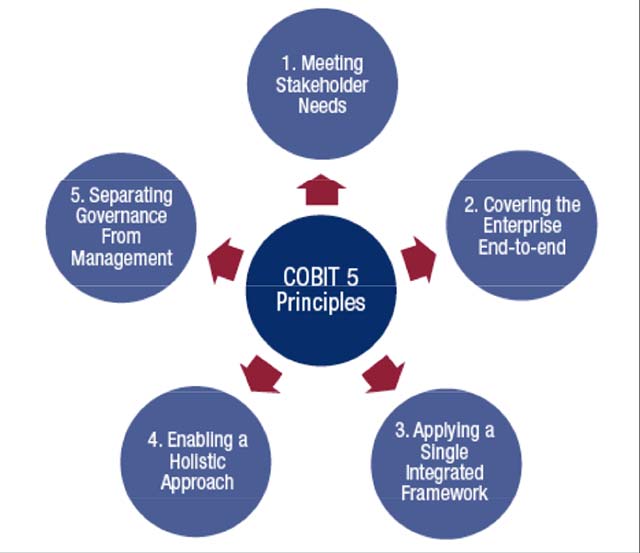 5 core principles of how COBIT works 5
5 core principles of how COBIT works 5
- The cyber security tools that every business should know
The goal of COBIT
The latest release of the COBIT framework has gathered the full set of guidelines since the fourth version, along with Val IT 2.0 and Risk IT Framework. According to ISACA, all of the above updates and changes mean the following:
- Streamline information sharing within the organization.
- Use information technology strategy and capabilities to achieve business goals.
- Minimize information security risks and provide more control options.
- Provide cost effective solutions for information technology deployment activities.
- Integrate the latest findings into the COBIT framework.
Companies using some frameworks like CMI and ITL will find their IT management tasks easier and more effective. In addition, stakeholders such as security experts, administrators, and information technology auditors may find that their work involves the entire scope of governance and management.
- Endpoint threat detection and response, an emerging security technology
Benefits of COBIT 5
It is not difficult to list some basic benefits that COBIT 5 brings to businesses. First, it allows businesses to deploy information security monitoring and management processes in a simpler and more efficient way. It also helps ensure the ability to manage vulnerabilities.
When it comes to risk management, COBIT 5 allows you to minimize risks to your business as well as be more proactive in establishing the necessary rules.
Overall, COBIT 5 provides a holistic perspective for businesses, integrating other standards, frameworks and strategies, such as ITIL and ISO / IEC 27001, into a complete business management and management framework.
- [Infographic] 5G network security: What carriers need to know
COBIT 5 framework
There are several components that make up COBIT 5, including:
The main framework
The main framework helps create basic guidelines, foundations, and best practices related to IT governance. These guidelines can then be adjusted and integrated according to the actual needs and requirements of the organization. The main purpose of the framework is to allow businesses to organize and structure their goals with information technology capabilities.
Process description
This allows an enterprise to have a model reference process model, along with the common language used by each member of that business. Descriptive factors include planning, creation, implementation, and monitoring of information technology related processes. This helps each individual in the organization understand and understand the processes and related terms.
Control the target.
Businesses can find a complete list of requirements needed to effectively control information technology related processes. This can certainly help improve the management and operation efficiency of all information technology processes of the enterprise.
Management guide
COBIT guidelines will detail the responsibilities of people and their specific tasks at each stage. In addition, they also show how an organization's performance is measured in COBIT 5 implementation.
Model complete
These models will assess the 'maturity' of businesses in terms of implementing processes and dealing with challenges.
- The rise of IoT Botnet and how to protect smart devices
COBIT 5 certificates
ISACA is the leading agency responsible for training and certification of COBIT 5, along with:
- How to apply COBIT 5 in any situation
- How to apply COBIT 5 with other management frameworks
- How to understand the challenges that COBIT 5 solves.
There are 2 ways to achieve COBIT 5 certification:
- Implementation: Focus more on the application of COBIT 5 in business models and challenges.
- Evaluation: More focused on how to review processes that require appropriate modification or modification.
COBIT certification will be extremely useful for every business as well as a number of management positions in the business such as information technology directors, managers, members of corporate audit committees etc.
- [Infographic] 7 effective ways to protect businesses from Ransomware
 COBIT certification will be extremely useful for all businesses and managers
COBIT certification will be extremely useful for all businesses and managers