New banking malware discovered that can remotely control Android devices
Octo Designed to target the Android operating system, this malicious code is dangerous in its ability to remotely access an infected system, allowing malicious actors to commit fraud on your device. flexible victim.
Octo is essentially an evolution of ExoCompact, an Android malware variant based on the Exo trojan that had its source code publicly leaked in 2018. Octo was first discovered by researchers at ThreatFnai while the situation was not clear. flag observed some users looking to buy it on darknet forums.
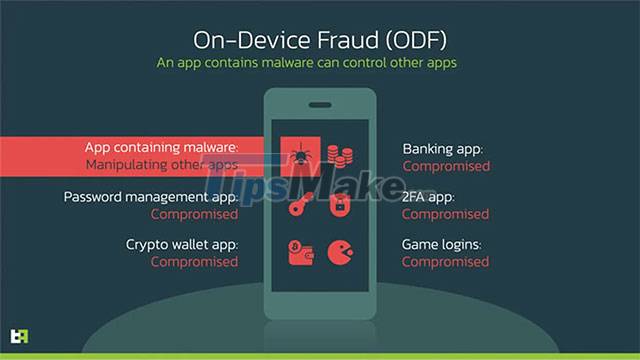
The possibility of cheating on the device
Octo's most notable innovation compared to ExoCompact is that it has an enhanced remote access module that allows threat actors to perform on-device fraud (ODF). by remotely manipulating the compromised Android device.

Remote access is provided through the screen live streaming module (updated every second) through Android's MediaProjection, and remote actions through the Accessibility Service.
Octo uses a black screen overlay to hide remote operations, sets the screen brightness to 0 and turns off all notifications by activating "no interruption" mode.
By turning off the device, the malware can perform various tasks without the victim's knowledge. Such as actions on the screen, gestures, writing text, modifying the clipboard, pasting data and scrolling up and down.
In addition to the remote access system, Octo also possesses a powerful keylogger, which can monitor and capture every action of the victim on infected Android devices. The information recorded includes PINs entered, web pages visited, number and location of clicks, as well as text modification activities.
Besides, this malicious code also supports an extensive list of commands, which can be mentioned as:
- Block push notifications from specific apps
- Enable SMS blocking
- Turn off the sound and temporarily lock the device's screen
- Launch a specific application
- Start/stop remote session
- Updated list of C2 . servers
- Open the specified URL
- Send SMS with specified text to a specified phone number
Contagion campaign
Octo is sold on some hacker forums, such as the famous Russian speaking hacker forum called XSS. Due to its many similarities with ExoCompact, including its presence on Google Play, its ability to disable Google Protect, and its reverse engineering protection system, the malware is believed to originate from the same organization. unidentified malicious.
Notably, ExoCompact also has a remote access module that, although simpler, also offers options to delay command execution and has an admin panel similar to Octo's.
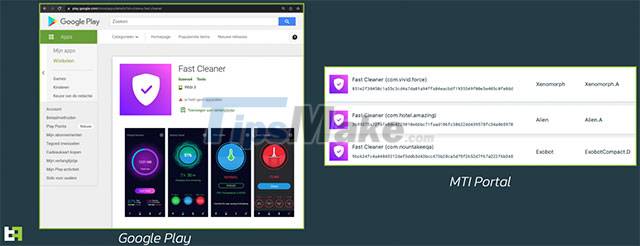
"Fast Cleaner" is one of several apps on the Google Play Store that contain Octo malware. This application was downloaded more than 50,000 times before being thought to be downloaded at the end of February.
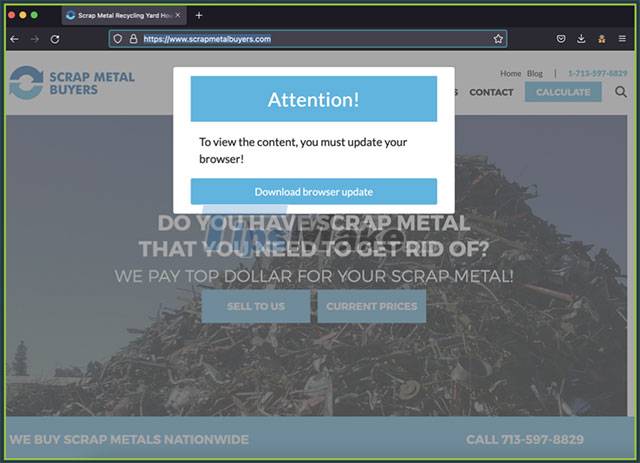
Several other Octo distribution campaigns are based on websites that use fake browser update notifications, or bogus app update warnings on the Play Store.
The full list of known Android apps that contain Octo malware is listed below:
- Pocket Screencaster (com.moh.screen)
- Fast Cleaner 2021 (vizeeva.fast.cleaner)
- Play Store (com.restthe71)
- Postbank Security (com.carbuildz)
- Pocket Screencaster (com.cutthousandjs)
- BAWAG PSK Security (com.frontwonder2), and
- Play Store app install (com.theseeye5)
In general, trojans with remote access modules are becoming more and more popular, making inherently robust account protection steps like two-factor authentication obsolete as the threat actor takes full control of the device. and logged in accounts. Whatever the user sees on their device's screen is within the reach of these malware variants, so after infection, no information is safe and no action can be taken. which protection measures are absolutely effective.
There is no other way than that users need to remain vigilant, keep the number of apps installed on their smartphones to a minimum and regularly check to make sure Play Protect is activated.
You should read it
- ★ Use SEO to bring Google search results to bank trojans
- ★ Trojan root Android device bypasses Google's security mode on Play Store
- ★ Hackers are taking advantage of the Store to distribute malware
- ★ New bank trojan detection on Android Red Alert
- ★ Discovering many applications containing malware on Google Play Store, Android users should worry gradually