GitLab patches critical vulnerability that allows hackers to take control of accounts
This vulnerability was discovered by GitLab employees themselves and is tracked under the code CVE-2022-1162. It affects both GitLab Community Edition (CE) and Enterprise Edition (EE).
CVE-2022-1162 comes from an inadvertently set static password during OmniAuth-based registration in GitLab CE/EE.
"Hard-coded passwords were set for accounts registered with OmniAuth providers (e.g. OAuth, LDAP, SAML) in GitLab CE/EE version 14.7 prior to 14.7.7, 14.8 prior to 14.8.5 and 14.9 before 14.9.2 allowed hackers to take control of the account," the GitLab team shared.
GitLab urges users to immediately upgrade all GitLab installations to the latest version (14.9.2, 14.8.5 or 14.7.7) to prevent the risk of being hacked.
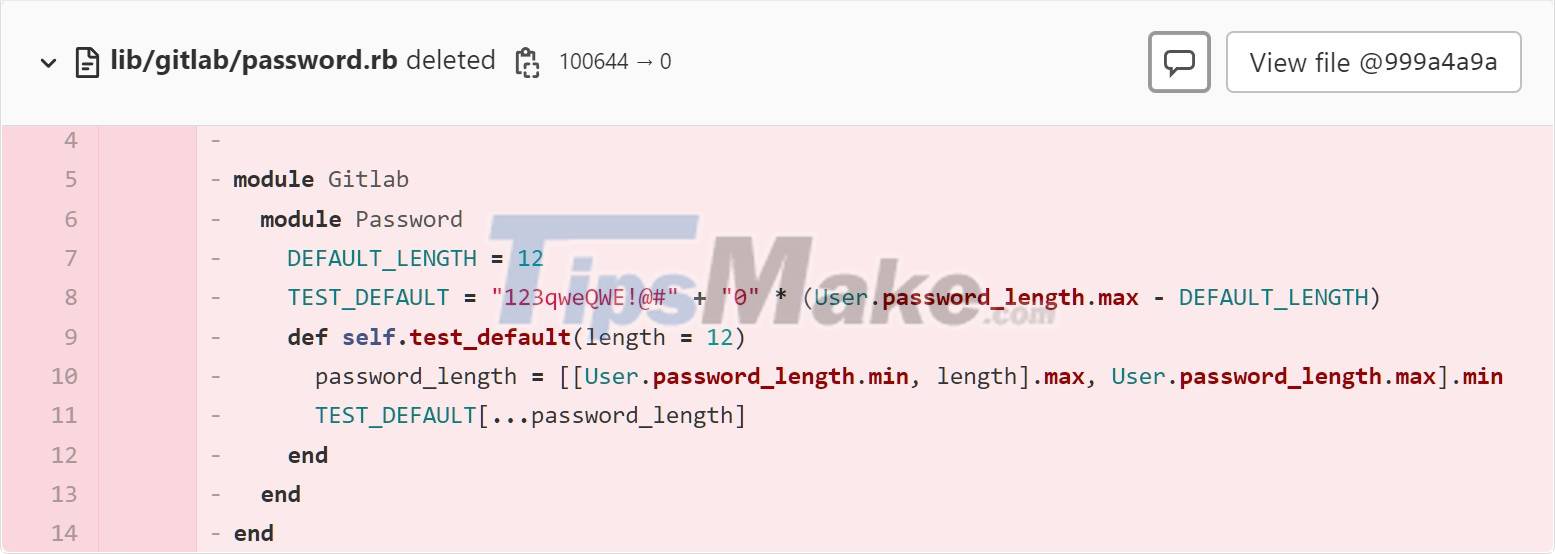
As part of an effort to mitigate the damage of CVE-2022-1162, GitLab said it has reset the passwords of some GitLab.com users. In addition, a recently submitted commit revealed that GitLab removed the file "lib/gitlab/password.rb" that was used to attach a weakly hard-coded password to the row number "TEST_DEFAULT".

GitLab says it has not seen any evidence of user accounts being compromised by hackers by exploiting this vulnerability. Even so, GitLab still creates a script that administrators can use to identify user accounts potentially affected by CVE-2022-1162. Details about the vulnerability and how to download the script can be found here.
Once a potentially affected user account is identified, an administrator should reset the user's password.
More than 100,000 organizations use GitLab's DevOps platform, and an estimated 30 million users from 66 countries are registered with the platform.
You should read it
- ★ 'Printer Catastrophe' Vulnerability Threatens All Versions of Windows
- ★ Log4Shell zero-day vulnerability discovered, the new nightmare of enterprises
- ★ Apple releases iOS 14.4.2, iOS 12.5.2, and watchOS 7.3.3 updates that patch the critical zero-day vulnerability
- ★ New privilege escalation vulnerability called 'Dirty Pipe' is threatening all Linux distros
- ★ The NSA issued an urgent warning about a critical vulnerability appearing in Windows servers