Detection of Windows SmartScreen vulnerability being exploited to spread DarkGate malware
A new wave of active DarkGate malware exploits a vulnerability in Windows Defender SmartScreen has now been upgraded, with the ability to bypass security checks and automatically install fake software installers plating on the target system.
SmartScreen is a Windows security feature that displays a warning when users try to run unrecognized or suspicious files downloaded from the internet. The vulnerability tracked, identified as CVE-2024-21412, is an issue in Windows Defender SmartScreen that allows specially crafted downloads to bypass security warnings from the company. this tool.
Attackers could exploit the vulnerability by creating a Windows Internet shortcut (.url file) that points to another .url file stored on a remote SMB share. This will cause the file in the last location to be executed automatically.
CVE-2024-21412 was patched by Microsoft in mid-February, but it seems that this update has not really been fully applied. Previously, Trend Micro revealed that a group of financial hackers nicknamed Water Hydra successfully exploited this vulnerability as a zero-day to spread their DarkMe malware into the systems of traders. pandemic.
Today, Trend Micro analysts continue to issue an urgent announcement that those behind the DarkGate malware are deploying a new wave of attacks, exploiting similar vulnerabilities to improve the chances of successful infection. attacks on targeted systems.
Details of the DarkGate attack
The attack begins with a malicious email that includes a PDF attachment containing a link that uses open redirects from Google's DoubleClick Digital Marketing (DDM) service to bypass email security checks.
When victims click on the link, they are redirected to a web server that hosts an internet shortcut file. This shortcut file (.url) in turn links to a second shortcut file hosted on a WebDAV server controlled by the attacker.

Using a Windows Shortcut to open a second Shortcut on a remote server effectively exploits the CVE-2024-21412 vulnerability, causing a malicious MSI file to automatically execute on the device.

These MSI files are masqueraded as legitimate NVIDIA software, Apple iTunes or Notion applications.
When executing the MSI installer, another DLL loading vulnerability involves the file "libcef.dll" and a loader named "sqlite3.dll" that decodes, and executes the DarkGate malware payload on the system .
Once initialized, malware can steal data, fetch additional payloads and inject them into running processes, perform key logging, and grant attackers access from away in real time.
The complex and multi-step infection chain used by DarkGate exploiters since mid-January 2024 is summarized in the diagram below:
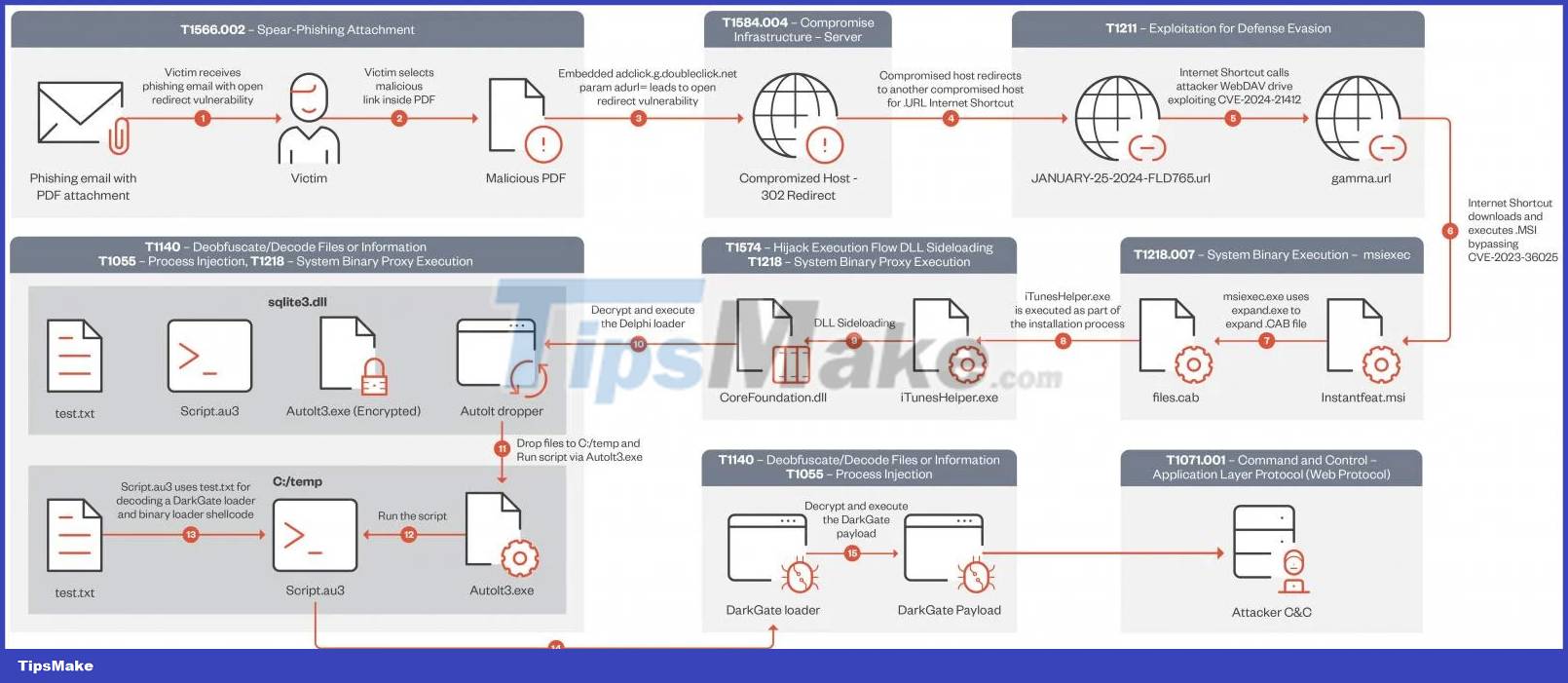
Trend Micro said this campaign used DarkGate version 6.1.7. Compared to the older version 5, version 6 features XOR-encoded configuration, new configuration options, and updates to command and control (C2) values.
The configuration parameters available in DarkGate 6 allow operators to define various operational tactics and evasion techniques, such as allowing persistent booting or specifying disk storage capacity and size. Minimum RAM to avoid analysis environment.
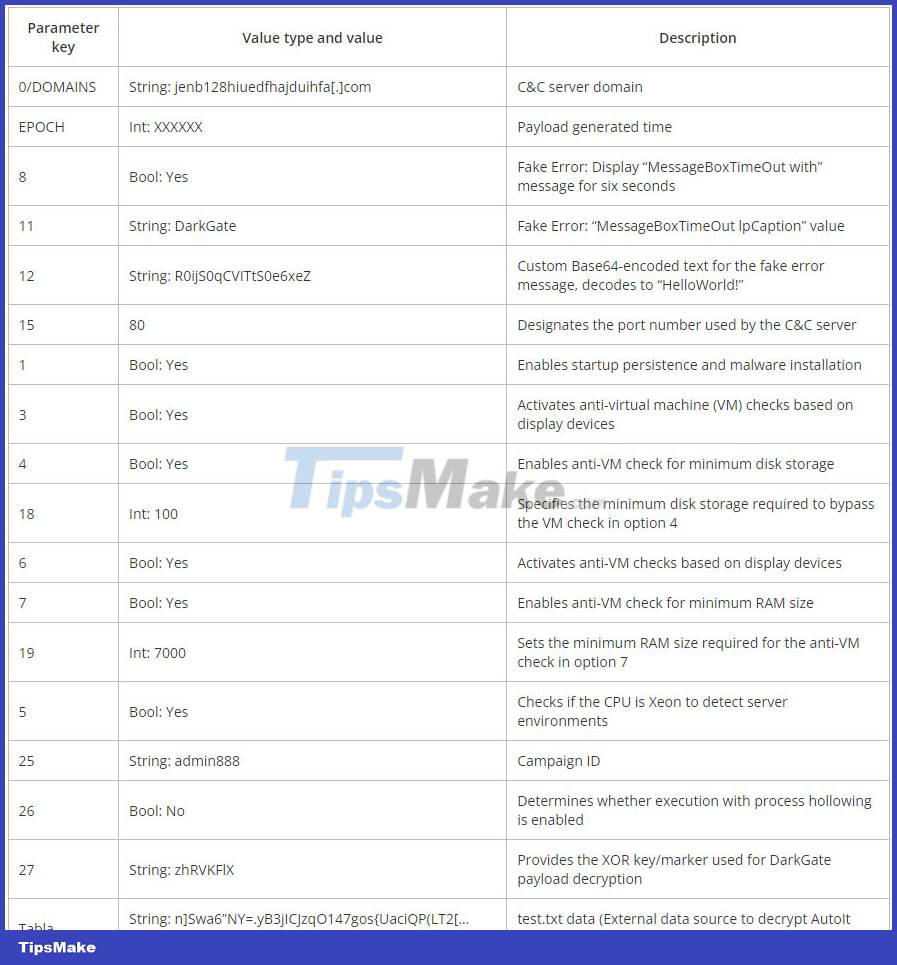
Currently, the only option to mitigate the risk from these attacks is to apply Microsoft's February 2024 Patch Tuesday update to fix the bug CVE-2024-21412.
You should read it
- ★ New malware discovered that can bypass Windows SmartScreen and steal user data
- ★ Summary of popular network attacks today
- ★ How to disable SmartScreen feature in Windows 8?
- ★ Instructions to enable or disable SmartScreen on Windows 10
- ★ Download and sell Windows patches for all versions to avoid being hit by a massive cyber attack, affecting 150 countries and still spreading