Face some new hacking techniques related to Bluetooth technology
Bluetooth is a connection technology that has been around for a long time and is probably no stranger to each of us. Bluetooth connectivity makes it easy to move files, photos and documents between devices, such as mobile phones, laptops and tablets, within a certain distance. That fast side, the same Bluetooth is used to connect and exchange data between a main device and peripheral devices such as phones with wireless speakers, headsets or smart watches .
In terms of development history, this wireless communication protocol was first introduced in 1998. It can be said that Bluetooth technology has helped revolutionize the ability of wireless communication between technology devices, along with It is extremely simple and useful features. However, even the most advanced technology achievements have certain weaknesses, Bluetooth is no exception. Besides the above convenience, this connection technology has inadvertently increased data security and privacy issues at the individual level.
 Hack via Bluetooth connection is no longer a rare phenomenon
Hack via Bluetooth connection is no longer a rare phenomenon
Hackers can easily take advantage of the vulnerabilities available in the Bluetooth protocol to deploy various infringing activities, such as: stealing personal data, installing malware and even taking over device control (rare). Security violations through Bluetooth connectivity are dangerous in that they can access a large number of different technology devices, such as mobile phones, laptops, tablets and systems. Car entertainment . In short, any device with Bluetooth connectivity technology is at risk of being hacked.
- AirPods and other types of Bluetooth headsets do not cause cancer. Where is the truth?
Bluetooth hack technique
- BlueBorne
- Btlejacking
- Bleedingbit
- CarsBlues
BlueBorne
BlueBorne is a relatively easy-to-exploit security vulnerability that exists in some Bluetooth versions. This vulnerability was first reviewed and published in April 2017 by security researchers from Armis. BlueBorne exists primarily on mobile operating systems, desktops and IoT, including Android, iOS, Windows and even Linux. Basically, this vulnerability could allow hackers to attack and gain control of the device, and trick users into providing information or silently stealing their information.
 BlueBorne was first discovered in April 2017
BlueBorne was first discovered in April 2017
Security researchers have explained the characteristics of attack vectors targeting BlueBorne as follows: 'In an attack against the BlueBorne vulnerability, the target device does not need to be paired with another device. contains a storage hard drive, or is configured in stealth mode '. Until now, the Armis Labs team has identified a total of six zero-day vulnerabilities that can allow the existence and potential of attack vectors to be shown.
Armis believes there are more security holes that can be found on different platforms using Bluetooth, and this BlueBorne vulnerability owns the necessary conditions, enabling the hacker to easily develop. Open the extraction process with a high success rate.
BlueBorne has gradually become a dangerous threat to devices with Bluetooth connectivity. Unlike most Internet-based malicious attacks that we often see, BlueBorne attacks spread through the 'offline' connection protocol. This means that hackers can silently connect to smartphones, computers and take control of the device without going through any user mistakes such as for internet-based attacks. .
- The best true wireless headphones on the market - when convenience comes to the throne
Btlejacking
Bussyjacking is a Bluetooth-based attack vector discovered and published in August 2018 as part of the Global DefCon hacker conference in Las Vegas. White hat hacker Damien Cauquil, Head of Research and Development Department of Digital Security is the one who has discovered this method of attack via Bluetooth.
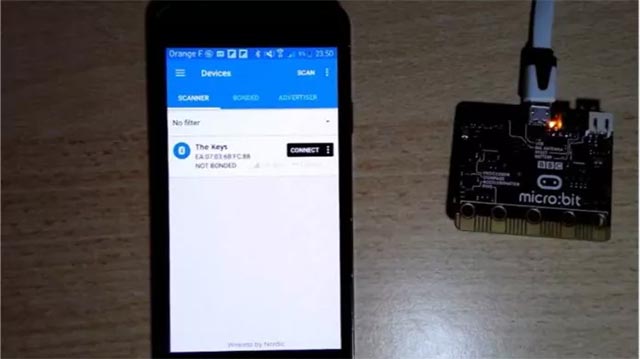 Bussyjacking technique only requires relatively simple support equipment
Bussyjacking technique only requires relatively simple support equipment
As explained by Cauquil, with this new hack technology, hackers can completely disconnect and infiltrate Bluetooth devices without users' knowledge. This is based on the jamming vulnerability identified with the CVE-2018-7252 identifier, which may affect Bluetooth-connected devices version 4.0, 4.1, 4.2 and even 5.0. . However, Bussyjacking contains a big weakness, that is, an attacker must appear in a radius of no more than 5 meters to take advantage of the CVE-2018-7252 vulnerability, so this attack vector cannot be hit. High prices in situations that require a lot of flexibility.
Still, the statistical results still show that there are hundreds of millions of highly capable Bluetooth devices worldwide attacked by Bussyjacking. After penetrating the device, Bussyjacking allowed hackers to discover, gather information about Bluetooth connections on the device, as well as block and control vulnerable Bluetooth devices.
To make a Bussyjacking attack targeting Bluetooth-connected devices, hackers just need to use a micro-integrated BIT computer that costs about $ 15, and a few lines of open source code.
- Hundreds of millions of Windows 10 computers are easily hacked due to errors in the original software of the manufacturer
Bleedingbit
Another case was discovered by security researchers from Armis. Specifically, the team discovered two new 'BleedingBit' vulnerabilities on Bluetooth chips that could affect many companies worldwide.
 BleedingBit is a hardware vulnerability that allows hackers to execute code remotely
BleedingBit is a hardware vulnerability that allows hackers to execute code remotely
The first vulnerability was codenamed CVE-2018-16986, allowing an attacker to execute remote code, involving four chip models embedded in seven Cisco access points and five access points of Meraki. If successfully exploiting this vulnerability, remote attackers can send dangerous Bluetooth data transfer messages. These messages are sometimes called 'ad packages', stored right on vulnerable memory chips. When a user activates Bluetooth, these malicious messages will quickly be 'awakened' to take up storage space, leading to 'memory overflow'. More seriously, they can also allow hackers to corrupt memory, access the operating system, create a backdoor, and execute malicious code remotely.
The second chip hole was identified as CVE-2018-7080, affecting almost all of the 300 access points of Aruba. Basically, this vulnerability allows an attacker to access completely new versions of the software (firmware) and install them.
BletingBit is mentioned as a wake-up call for enterprise security systems for two reasons:
'First, an attacker can get into the network without any signs or warnings that will exacerbate the inherent security concerns. Second, these vulnerabilities can destroy the network segment - the main security strategy that most businesses use to protect their systems from unidentified IoT devices or threats yet. known. And here, the access point can be considered an unmanaged device, 'said Yevgeny Dibrov, Armis CEO, in a blog post.
- Hackers use Raspberry PI computer to steal 500 MB of NASA important data
CarsBlues
Researchers from Privacy4Cars have discovered a relatively large new vulnerability, related to Bluetooth connectivity in the information and entertainment systems of different types of transport: CarsBlues . The attacks targeting this vulnerability can be done in minutes, with the participation of only a few available, low-cost hardware and software equipment, allowing hackers to delete received information. Personal format (PII) is removed from the user's system, regardless of whether they have synchronized their mobile phones with car entertainment systems via Bluetooth connectivity.
 CarsBlues targets cars information and entertainment systems
CarsBlues targets cars information and entertainment systems
It is estimated that tens of millions of vehicles worldwide are currently victims of CarsBlues-based attacks.
Hackers took control of the city's entire computer system, demanding a ransom of $ 600,000 bitcoin
The above is the basic information about some security vulnerabilities related to Bluetooth communication protocol and dangerous attack methods based on these vulnerabilities. Bluetooth-based attacks are generally not too common, nor do they cause great damage like normal network attacks, but getting more knowledge about them is what we should do.
You should read it
- ★ Apple announced a new, more diverse level of security bug detection bonus
- ★ iPhone and Android smartphone series stick with serious Bluetooth security error
- ★ A new security flaw allowed to impersonate Bluetooth peripherals
- ★ How to hack WiFi passwords with holes on WPA / WPA2
- ★ More than 1,300 phishing kits are being sold on the hacker forum